Overview
The Azure Bastion service is a fully platform-managed PaaS service that you provision inside your virtual network. It provides secure and seamless RDP/SSH connectivity to your virtual machines directly in the Azure portal over TLS. When you connect via Azure Bastion, your virtual machines do not need a public IP address.
Bastion provides secure RDP and SSH connectivity to all of the VMs in the virtual network in which it is provisioned. Using Azure Bastion protects your virtual machines from exposing RDP/SSH ports to the outside world, while still providing secure access using RDP/SSH. With Azure Bastion, you connect to the virtual machine directly from the Azure portal. You don’t need an additional client, agent, or piece of software.
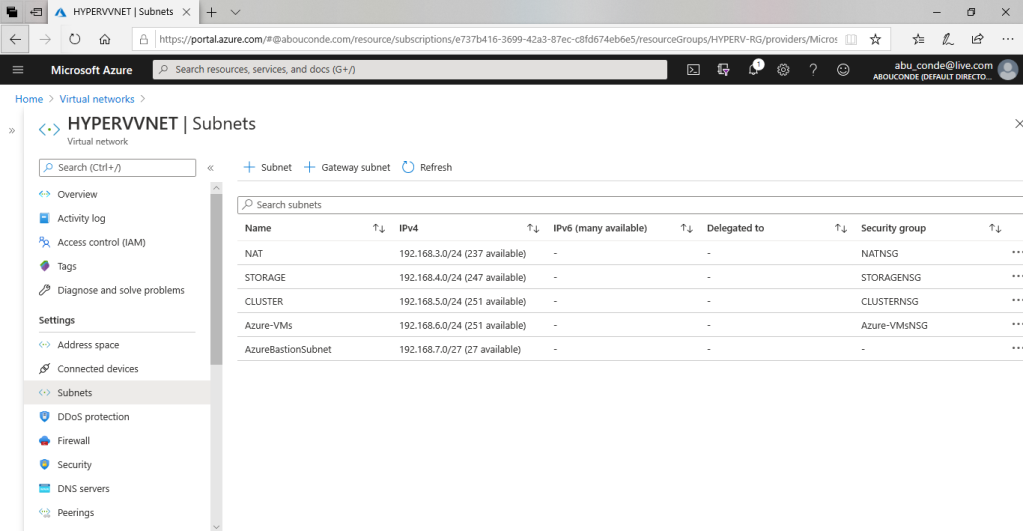
1. Add AzureBastionSubnet
The subnet will be dedicated to the Bastion host and must be named as AzureBastionSubnet. This subnet must be at least /27 or larger.
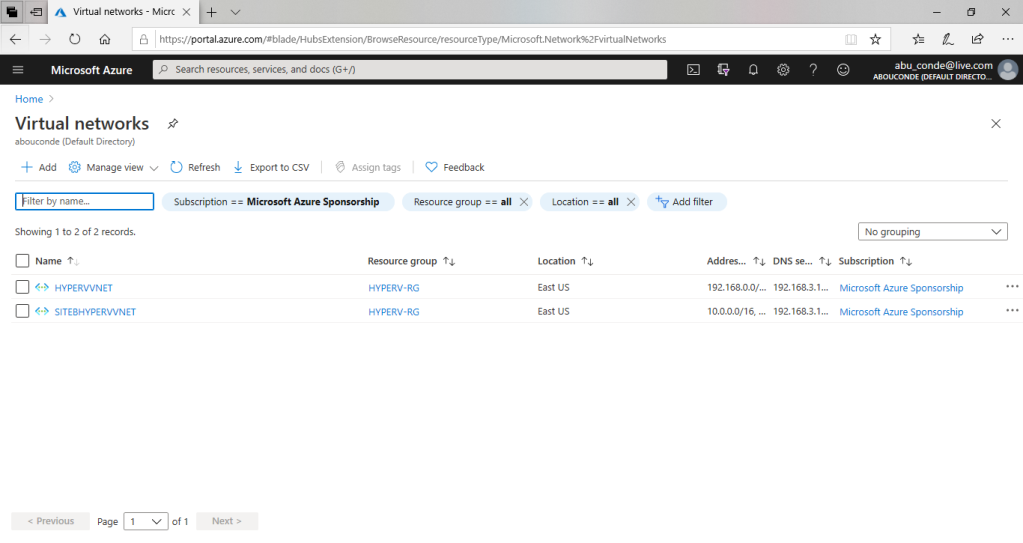
Go to the Azure portal to view your virtual networks. Search for and select Virtual networks.
Select the name of the virtual network you want to add a subnet to.
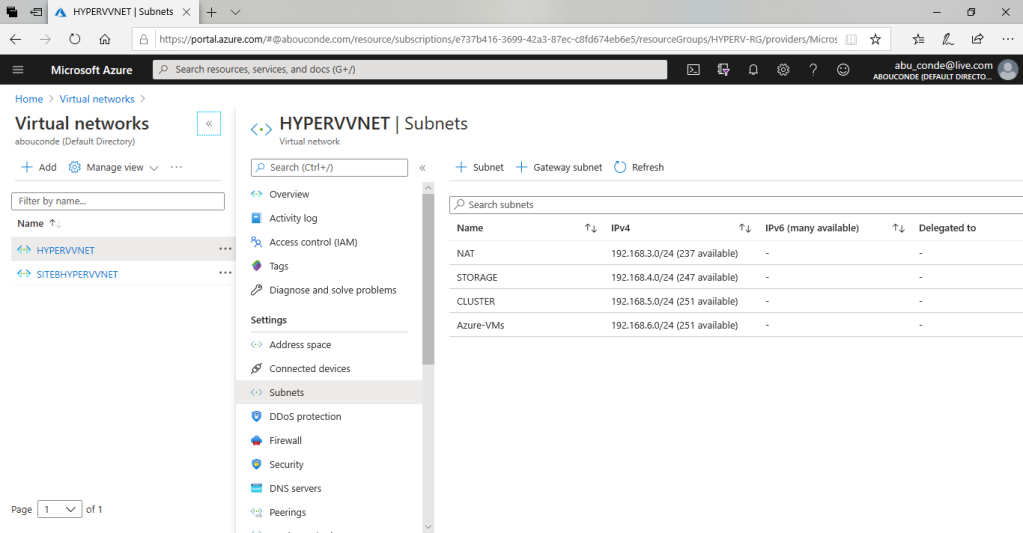
From Settings, select Subnets > Subnet.
In the Add subnet dialog box, enter values for the following settings:
Name: AzureBastionSubnet
Address range (CIDR block) : 192.168.7.0/27
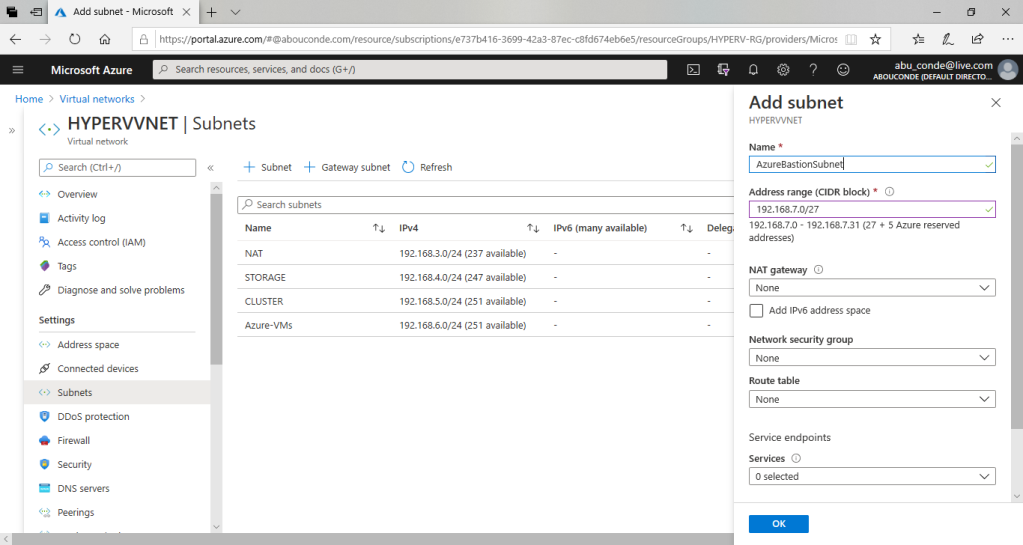
To add the subnet to the virtual network that you selected, select OK.
2. Create a bastion host
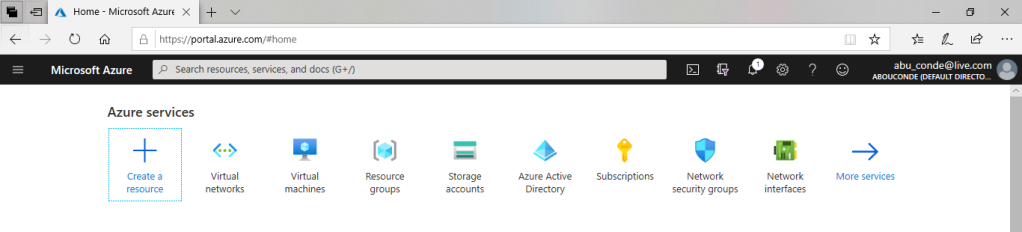
On the Azure portal menu or from the Home page, select Create a resource.
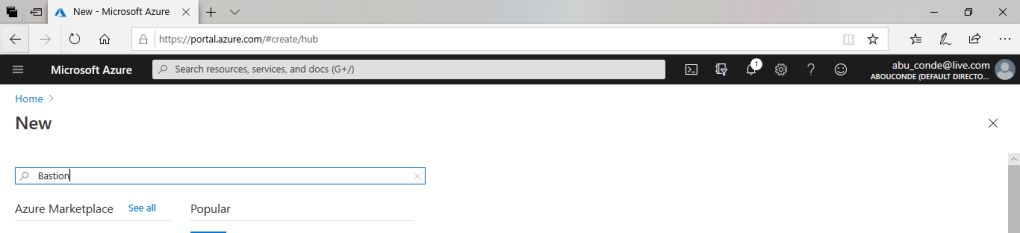
On the New page, in the Search the Marketplace field, type Bastion, then click Enter to get to the search results.
From the results, click Bastion. Make sure the publisher is Microsoft and the category is Networking.
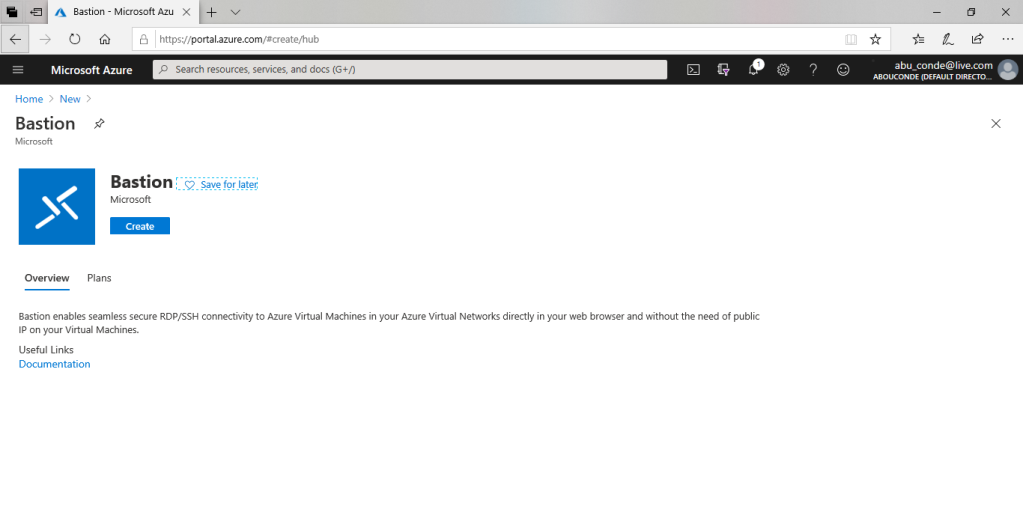
On the Bastion page, click Create to open the Create a bastion page.
On the Create a bastion page, configure a new Bastion resource. Specify the configuration settings for your Bastion resource.
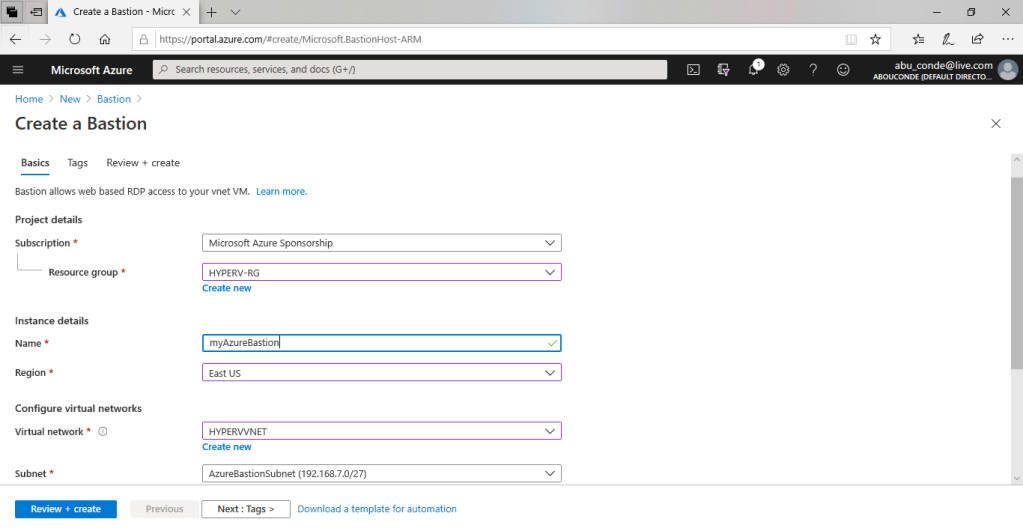
When you have finished specifying the settings, click Review + Create. This validates the values. Once validation passes, you can begin the creation process.
On the Create a bastion page, click Create.
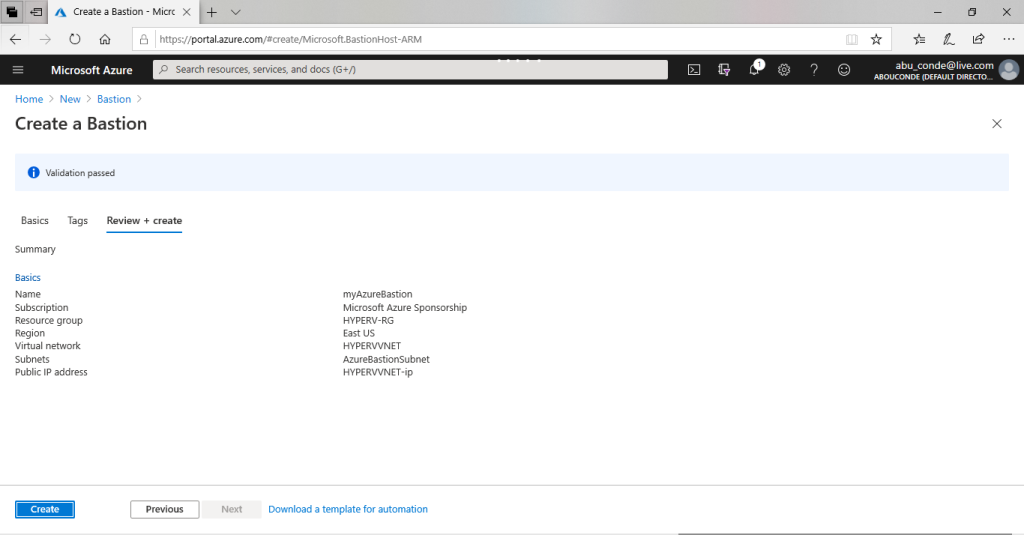
You will see a message letting you know that your deployment is underway. Status will display on this page as the resources are created. It takes about 5 minutes for the Bastion resource to be created and deployed.

Done
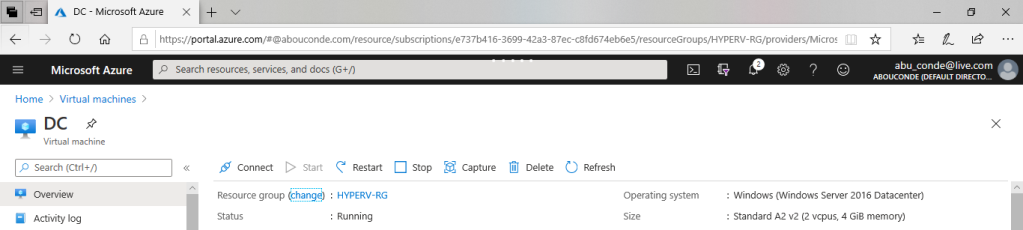
3. Connect to a VM using Azure Bastion
Open the Azure portal. Navigate to the virtual machine that you want to connect to, then click Connect and select Bastion from the dropdown.
After you click Bastion, a side bar appears that has three tabs – RDP, SSH, and Bastion. If Bastion was provisioned for the virtual network, the Bastion tab is active by default.
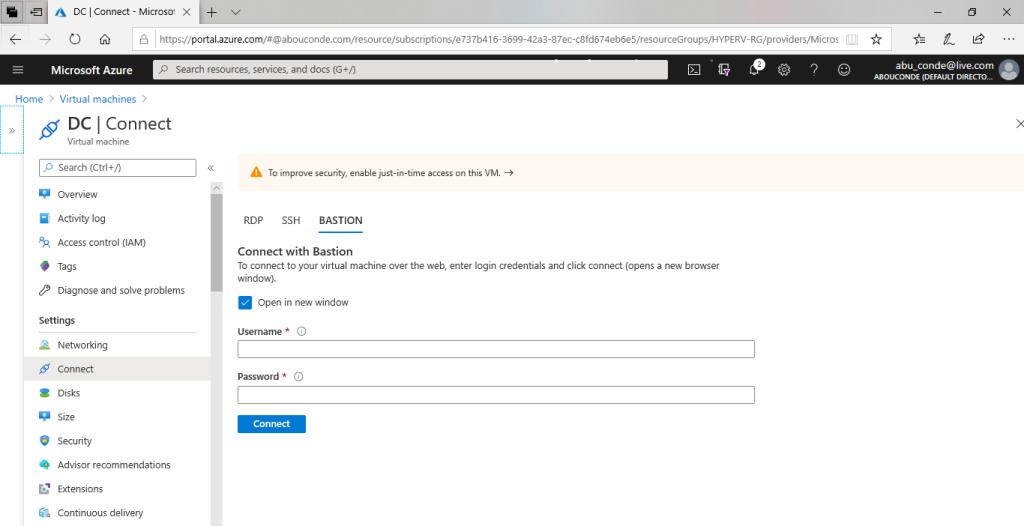
On the Bastion tab, input the username and password for your virtual machine, then click Connect. The RDP connection to this virtual machine via Bastion will open directly in the Azure portal (over HTML5) using port 443 and the Bastion service.
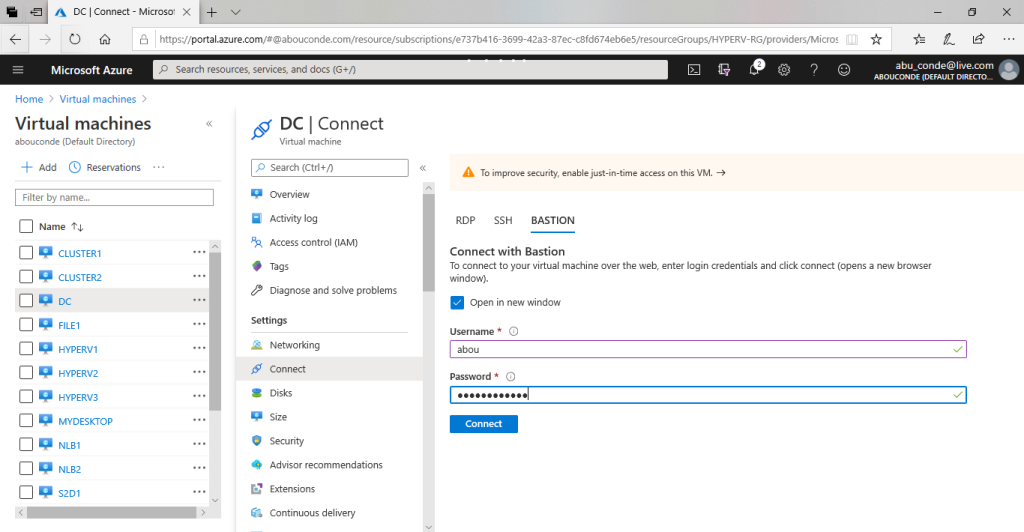
Connected